Overview
This guide provides step-by-step instructions for enabling multi-factor authentication (MFA).
What is MFA?
Multi-Factor Authentication (MFA) or Two-Factor Authentication (2FA) is an essential security feature that adds an extra layer of protection to your Built account. It helps prevent unauthorized access and fraud by requiring users to verify their identity through a secondary method beyond just a password. Built has adopted a "most-protective" approach to security in compliance with state regulations and to better safeguard user information and payment transactions.
How to Enable MFA
Step 1
Log into your Built account at id.getbuilt.com.
Note
The MFA requirement is only enforced on accounts that are receiving payments through Built. You will not be prompted to set up MFA when logging in until you have completed Business Verification.
Step 2
You will see a screen asking to enable Two-Factor Authentication. You can choose between using SMS text messages or a third-party authenticator app.
For SMS Text Message: Enter your phone number to receive a verification code.
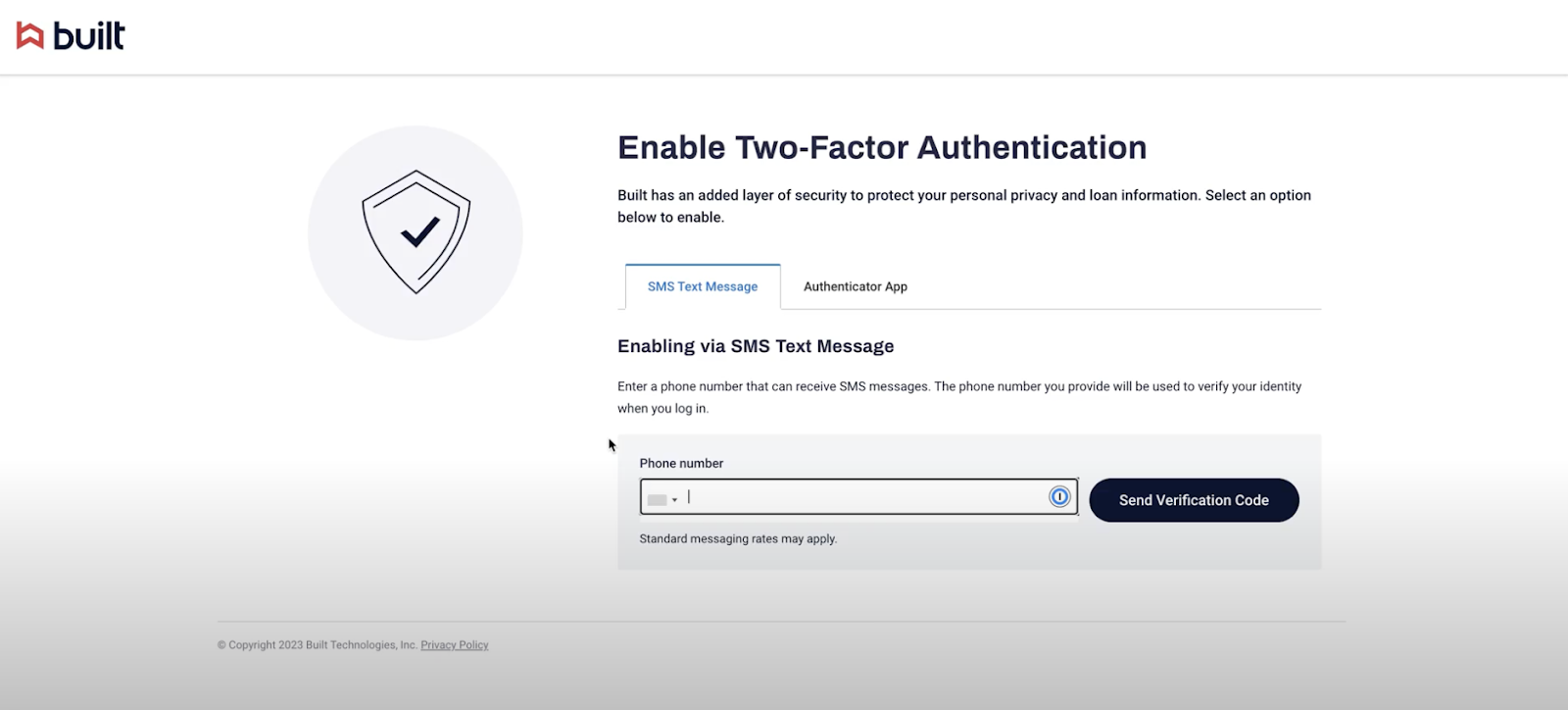
You’ll receive a text message with a 6-digit code. Enter the code in the open text field provided.
Click “Confirm”.
For the Authenticator App: Scan the QR code within your authenticator app to receive a verification code.
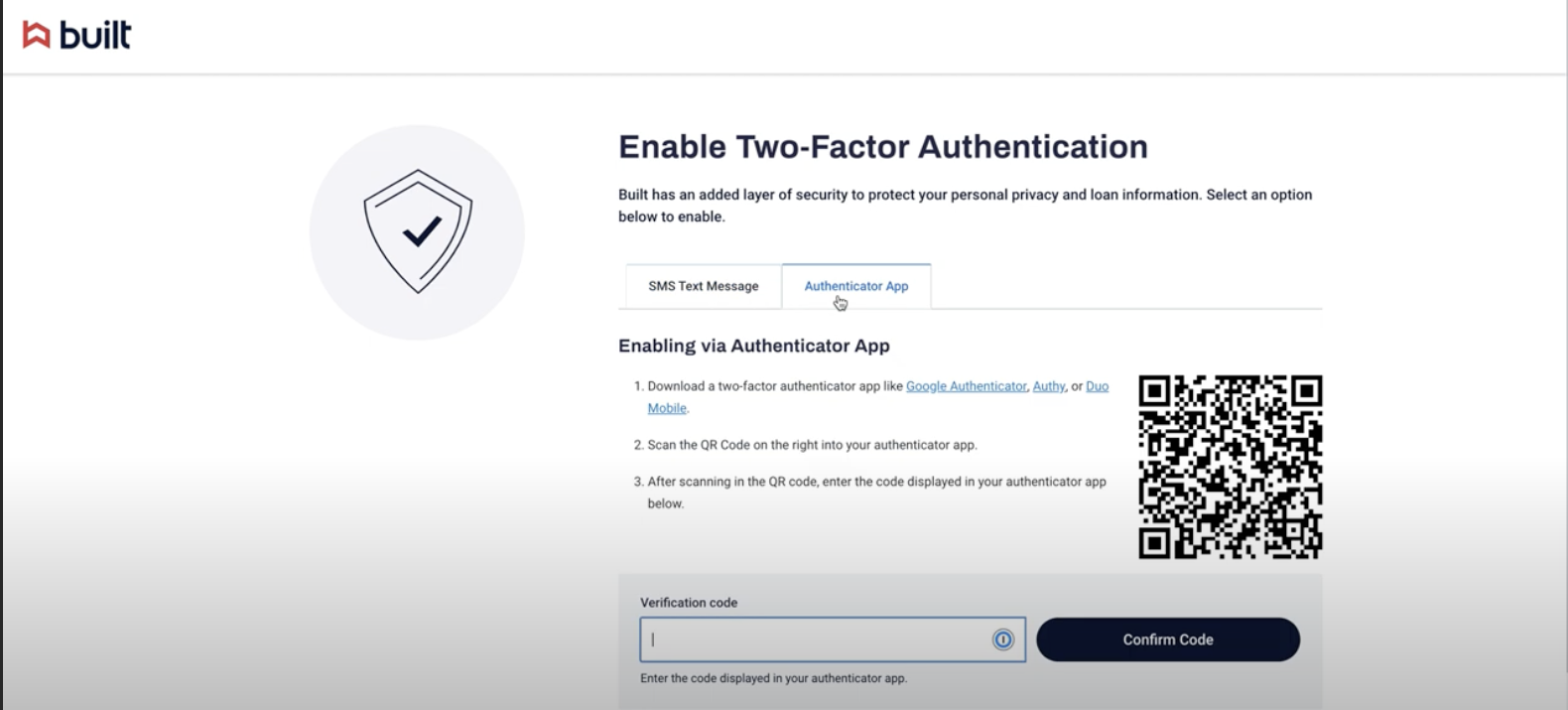
Open your preferred authenticator app on a mobile device or iPad/tablet.
Scan the QR code shown on your screen within Built. Enter in the one-time code generated by the app.
Click “Confrim”.
Step 3
Upon successful confirmation of the code, MFA will be enabled for your account.

The next time you log in, you will be prompted to enter a verification code to confirm your identity.

MFA Troubleshooting and FAQs
Is MFA required for every user?
Yes, MFA will be enforced for every user, both on the Built Inspect App (versions 4.0.16 and above) and on Built Desktop upon each login session.
Is MFA required on each login session?
Yes, MFA will be required upon every login. However, if you are using the same device, enable the "Remember this device?” option when logging in through your MFA method. With device memory enabled, you will only need to use MFA to log in every 90 days. Note: if you switch devices, you will need to re-enable MFA on your new device.

What MFA authenticator app can I use?
You can use any MFA authenticator app you prefer. Built recommends Google Authenticator, Microsoft Authenticator, or Duo Mobile as the most popular options.
Do I have to set up MFA again if I change my phone number?
If you have selected SMS as your authenticator method and change your phone number, you will need to re-enable MFA. Contact Built Support for assistance.
Can I log in with MFA even if I don’t have cellular service?
If you have selected SMS as your authenticator method, service will be needed to receive a text message. For this reason, Built recommends choosing an Authenticator App for any users who may use Built when out of service areas (ie, Built Inspectors)
Can I use both SMS and Authenticator App methods?
No, currently MFA setup requires users to choose one method. However, the method chosen can be changed at any time. See How to edit your MFA method after setup above.
What if multiple people use the same email address (account) to login to Built?
Shared credentials are generally not recommended for security reasons, however, this may be standard practice for some organizations. If multiple people use the same account in Built, setup MFA using the Authenticator App method only.
Can I receive an MFA code through my email?
No, currently the available MFA methods are SMS and Authenticator App’s only.
Do I need a QR code every time I login through MFA using an Authenticator App?
No, the QR code that displays is only for setting up MFA through the Authenticator App. Once MFA is enabled, users login through the code displayed within the Authenticator App.
How long are MFA codes valid before they expire?
Authenticator app codes (e.g., Google Authenticator, Authy): These typically expire every 30 seconds, which is standard for time-based one-time passwords (TOTP).
SMS codes: These are valid for up to 3 minutes after they are sent.
Why is my device not remembering me?
Some clients may experience repeated MFA prompts even when selecting “remember my device” due to their organization’s internal security configurations. Common factors include strict browser or endpoint policies that clear cookies or local storage after each session, virtual desktop environments that generate new device identifiers on login, or network policies that enforce frequent authentication resets. Because Built’s “remember my device” feature relies on secure browser tokens stored locally, these security measures can prevent the setting from persisting across sessions. We recommend that users reach out to their internal IT team to understand what configuration options may be available to allow trusted devices to be remembered while still maintaining their organization’s security requirements.